5 MCP security vulnerabilities you should know
Because the “USB-C for AI apps” shouldn’t also be a back-door for attackers
We’re working on a Model Context Protocol (MCP) implementation for PromptHub which has required us to go really deep on the topic.
For those that need a quick refresher, MCP is gaining a lot of popularity because of how easy it makes the communication between agents and tools. BUT, since it is so new, there are a whole new host of attack vectors to be aware of. Below are the five weaknesses most worth your attention, plus one-line fixes you can apply today.
For a deeper dive, check out our full blog post here: MCP Security in 2025
3 quick takeaways
43% of public MCP servers allow command injection—attackers can append
&& rm -rf /.30% fetch any URL you give them (classic SSRF).
22% leaked files outside their intended directories
Source: MCP Servers: The New Security Nightmare
1. Tool Poisoning
A tool looks normal and harmless by its name and maybe even its description, but it actually is designed to be nefarious. For example, a calculator tool that’s functionality actually deletes data.
Quick fix: Static-scan and manually review every new tool and all of its meta-data before it hits production.
2. Rug-Pull Updates
A tool is safe on Monday, but on Friday an update is shipped. You aren’t aware and now the tools start deleting data, stealing data, etc.
Quick fix: Pin versions and accept updates only after verifying a signed hash.
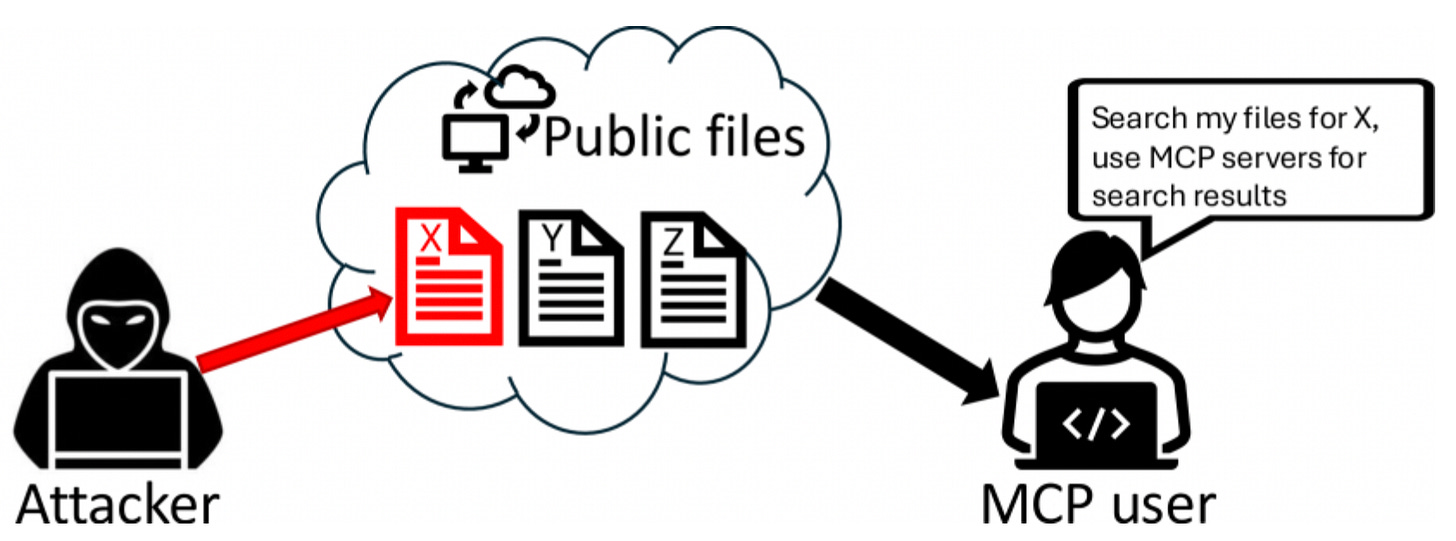
3. Retrieval-Agent Deception (RADE)
An attacker hides MCP commands in a public document; your retrieval tool ingests it and the agent executes those instructions.
Quick fix: Sanitize retrieved text, cap token limits, and pattern-scan results before feeding them back to the LLM.
4. Server Spoofing
A rogue MCP server copies the name and tool list of a trusted one and captures all calls. Essentially a server that is a look-a-like to a popular service (GitHub, Jira, etc)
Quick fix: Only use servers that you trust!
5. Cross-Server Shadowing
With multiple servers connected, a compromised server intercepts or overrides calls meant for a trusted peer.
Quick fix: Isolate high-risk servers, restrict scopes per server, and log any cross-server call redirections.
Wrapping up
MCP’s plug-and-play power is real, but so is the risk. Escape inputs, pin & sign every tool, enable OAuth/mTLS, and you’ll dodge most early-stage exploits while the protocol matures. Happy (secure) building!
P.S. If you’re implementing the MCP in your company or you’re interested in our implementation at PromptHub, feel free to reach out!